Belgium / Info / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at edpnet customers.
The email with the subject “Nouveau message:” pretends to come from edpnet service desk and contains a phishing link.
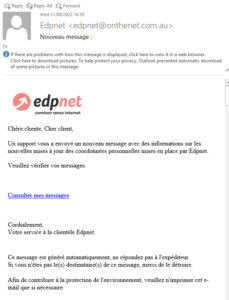
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Belgium / Info / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at edpnet customers.
The email with the subject “Bevestig/update uw Edpnet webmail” was sent yesterday at around 15h00 and contains a phishing link.
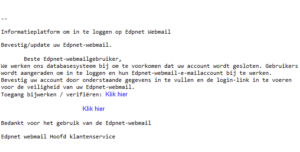
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Belgium / Info / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at edpnet customers.
The email with the subject “Edpnet: Undelivered messages received on Tuesday, August 23, 2022” pretends to come from edpnet service desk and contains a phishing link.
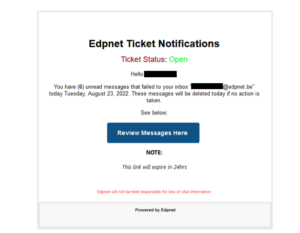
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Belgium / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at edpnet customers.
The email with the subject “Vous avez des messages électroniques en attente” pretends to come from edpnet service desk and contains a phishing link.
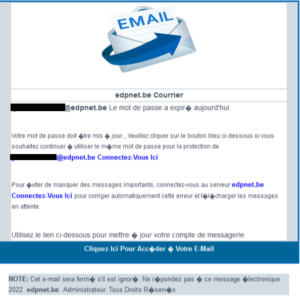
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Belgium / Info / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at edpnet customers.
The email with the subject “Security-Notification” pretends to come from edpnet service desk and contains a phishing link.
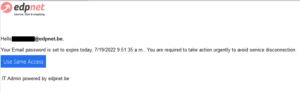
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Info / Maintenance / Netherlands / Planned /
Dear customers,
KPN has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
28-07-2022 01:00 |
| End*: |
28-07-2022 07:00 |
| Duration: |
expected impact: 2 hours 30 minutes |
| Impacted services: |
all internet services |
| Affected Areas**: |
The Netherlands: all areas |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at both customers and non-customers.
Customers receive emails with a fake delivery notice, pretending to come from edpnet and containing a phishing link.
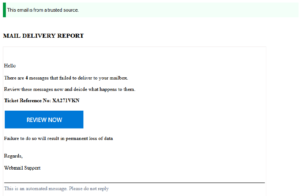
Please do not reply to those emails and do not click on the link. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Maintenance / Netherlands / Planned /
Dear customers,
Please be informed that the maintenance we announced earlier for the Netherlands has been postponed to 28/06/2022.
This maintenance will cause multiple short disconnections during the scheduled window.
Please find all details below:
| Start*: |
28/06/2022 00:00 |
| End*: |
28/06/2022 06:00 |
| Duration: |
expected impact: multiple short disruptions |
| Impacted services: |
all internet services |
| Affected Areas**: |
the Netherlands: all areas |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Info / Maintenance / Netherlands / Planned /
Dear customers,
We have planned a maintenance on our core routers in order to improve the performance and the quality of our services.
The maintenance will cause multiple short disconnections during the scheduled window.
Please find all details below:
| Start*: |
27-06-2022 00:00 |
| End*: |
27-06-2022 06:00 |
| Duration: |
expected impact: multiple short disruptions |
| Impacted services: |
all internet services |
| Affected Areas**: |
the Netherlands: all areas |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Internet / Netherlands / outage / Telephony /
Dear customers,
We are currently experiencing an distributed denial of service attack (DDoS) on all of our services. This may cause you to experience problems with all of our services. Our Network Operations team is investigating this outage. Further updates will be released as soon as possible.
Please find all details below:
| Start*: |
15-09-2021 16:15 |
| End*: |
19-09-2021 22:24 |
| Duration: |
// |
| Impacted services: |
All services are impacted |
| Affected Areas**: |
All areas |
EDIT 16:44*: As soon as we identified the issue, we have started routing our data through a scrubbing service (which tries to identify harmful sources & data and removes it).
EDIT 17:19*: The situation seems to be improving as we identify more and more attack vectors and sources. It seems like for most impacted customers, the situation has improved markedly since approximately ~17h.
EDIT 16/09/2021 10:12*: During the night we had two more attacks. We are working with the authorities, who have confirmed they are looking into it and are doing everything in their power to find the responsible individuals. We were contacted by an individual who verified he was behind the attacks, asking for a ransom.
EDIT 13:18*: We are being DDoS’ed again. We are doing what we can to mitigate the issues.
EDIT 15:41*: The attacks are still on-going. To give you a perspective of what we are dealing with, this is what our filtering service has been able to filter out so far:
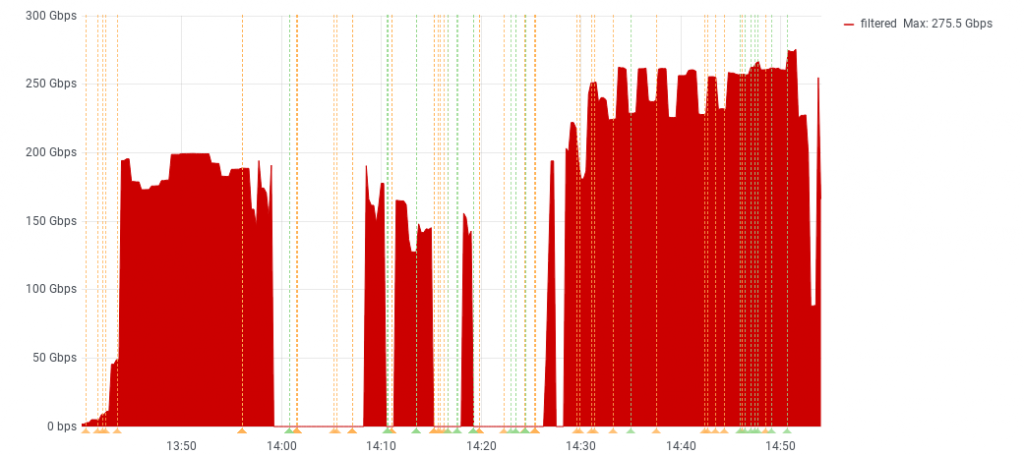
EDIT 16:39*: We are monitoring the situation closely, and are discussing the situation both with our anti-DDoS provider and Belgian official instances. We hope to improve the situation as soon as possible and will keep you in the loop of our progress.
EDIT 17/9 15:47*: The attacks have started again. All of our uplinks are entirely congested. We are trying to mitigate the DDoS once more.
EDIT 18/09 12:41*: Yesterday evening and past night we were hit with multiple attacks. Currently no attacks since 03:00. We still expect more attacks to come. We are monitoring 24/7. And we will communicate accordingly. We try to answer questions or comments on social media as good as we can.
EDIT 20/09 9:48: There were some attacks on Sunday afternoon. No new attacks since then. We keep monitoring and do our best to minimize impact in case of new spikes.
We apologize for the inconveniences.
Best regards
The edpnet team
*All times are listed in CET, Central European Time
** Check the different areas & zones on our support site






