Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance in order to move some underground cables before the road works.
This maintenance may affect your services.
Please find all details below:
| Start*: |
09-09-2021 00:15 |
| End*: |
09-09-2021 06:00 |
| Duration: |
5 hours 45 minutes |
| Impacted services: |
all internet services |
| Affected Areas**: |
Roeselare,
Ronse |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
27-08-2021 00:00 |
| End*: |
27-08-2021 06:00 |
| Duration: |
6 hours |
| Impacted services: |
all internet services |
| Affected Areas**: |
Herstal,
Oupeye,
Habay |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance in order to move some underground cables before the road works in the regions Forest and Saint-Gilles.
This maintenance may affect your services.
Please find all details below:
| Start*: |
25-08-2021 00:00 / 26-08-2021 00:00 |
| End*: |
25-08-2021 06:00 / 26-08-2021 06:00 |
| Duration: |
25-08-2021: 6 hours at night
26-08-2021: 6 hours at night |
| Impacted services: |
all internet services |
| Affected Areas**: |
Forest, Saint-Gilles |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Maintenance / Planned /
Dear customers,
Edpnet has planned a maintenance on one of our core routers in order to improve the performance and the quality of our services. These works may cause a short interruption of your connection during scheduled maintenance window.
Please find all details below:
| Start*: |
24-08-2021 02:00 |
| End*: |
24-08-2021 05:00 |
| Duration: |
potential impact: a short interruption of internet connection during maintenance window |
| Impacted services: |
all internet services |
| Affected Areas**: |
02STR: Brussels region |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Domain / Solved /
Dear customers,
We would like to inform you about an issue we had on our dnsbelgium.be platform. Due to human error, a pre-set group of name servers (ns1 & ns2.edpnet.be) were changed as a whole rather than for a single domain, causing a temporary outage for domains managed under this group. Some of our .be-domains were affected this way.
The error was made at approx 11h50* and corrected at 13h30*.
We apologize for the inconvenience. If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
*local time
Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
08-07-2021 00:00 |
| End*: |
08-07-2021 06:00 |
| Duration: |
potential impact: up to 6 hours |
| Impacted services: |
all internet services |
| Affected Areas**: |
Diest;
Eeklo |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
25-06-2021 00:00 |
| End*: |
25-06-2021 06:00 |
| Duration: |
potential impact: up to 6 hours |
| Impacted services: |
all internet services |
| Affected Areas**: |
Ohey |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Maintenance / Planned / Scheduled /
Dear customers,
Proximus has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
10-06-2021 00:05 |
| End*: |
10-06-2021 06:00 |
| Duration: |
5 hours 55 minutes |
| Impacted services: |
all internet services |
| Affected Areas**: |
Oudsbergen |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
Belgium / Info / Mail / Netherlands / Phishing /
Dear customers,
We would like to inform you about a new phishing wave that is aimed at both customers and non-customers.
Customers receive emails pretending to come from a mailserver / support center, etc. The message tells you that your mail storage quota has been exceeded and incoming mails have been placed on hold until you click on a link.
Here is an example:
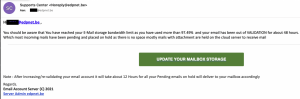
This is a blackmail spam and opening the link may cause a leak of your logins.
Please do not reply to those emails and do not open any files or click on any links. For more information, please, consider reading through our support article on this subject
https://www.edpnet.be/en/support/troubleshooting/internet/learn-about-security/phishing.html
If you have any questions left, please do not hesitate to contact us.
Best regards
The edpnet team
Belgium / Info / Maintenance / Planned /
Dear customers,
Proximus has planned a maintenance which may affect your services.
Please find all details below:
| Start*: |
22-04-2021 00:00 |
| End*: |
22-04-2021 06:00 |
| Duration: |
6 hours |
| Impacted services: |
all internet services |
| Affected Areas**: |
Boom |
We apologize for the inconveniences.
Best regards
The edpnet team
* All times are listed in CET, Central European Time
** Check the different areas & zones on our support site
